About a week prior to my presentation, the 100 prospective attendees received an email from me. In that email, I asked that the recipients review a slide for my upcoming presentation by clicking on an embedded link which routed them to a site that looked like Google Docs. At that site, they were asked to supply their email again. On the day before my presentation, I received no fewer than 12 phone calls from people who wanted to help and had tried unsuccessfully to review the slide after repeatedly clicking on the link.How would you feel if you found out 57 percent of your organization clicked on the link from a phishing email simulation? I pondered this question in the aftermath of the results of a phishing simulation I recently conducted. It involved a group of about 100 people who were prospective attendees at a local chamber of commerce event where I would be presenting. After considering the circumstances, I concluded two things: (1) the manner in which we conducted the phishing simulation made clear why this type of attack is so successful; and (2) this event presents an opportunity for in-house counsel to educate the C-suite and the organization about cybersecurity as a strategic enterprise business risk.
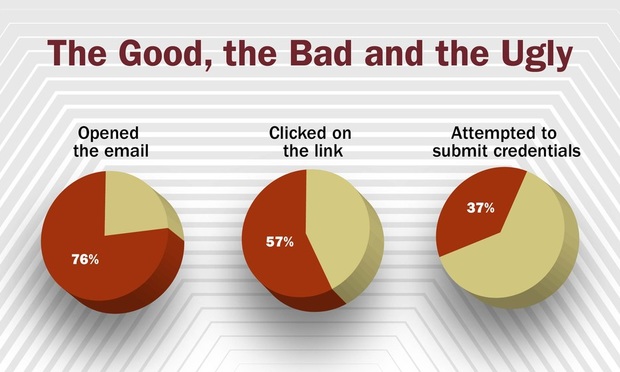
About 10 minutes into my presentation the following day, I asked the audience if they might have received a phishing email in the last few days. As the question hung in the air, I saw some sheepish looks as many realized where I was taking the conversation. The results of the simulation got everyone’s attention: 76 percent opened the email; 57 percent clicked on the link; and 37 percent repeatedly tried to submit credentials, which could not be accepted.

 (Photo: Billion Photos/Shutterstock.com)
(Photo: Billion Photos/Shutterstock.com)
